Connecting via Reverse SSH Tunnel
This page walks through connecting your data sources via a Reverse SSH Tunnel
Getting Started
Setup
version: "3"
services:
agent:
restart: always
image: "secoda/agent:latest"
environment:
- SSH_PORT=
- SSH_HOST=
- SSH_LISTEN_PORT=
- SSH_KEY_BASE64=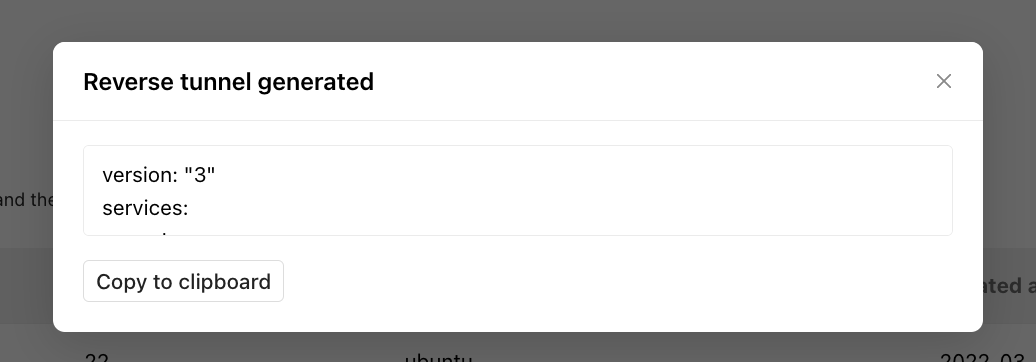
Running
docker-compose (recommended)
Custom
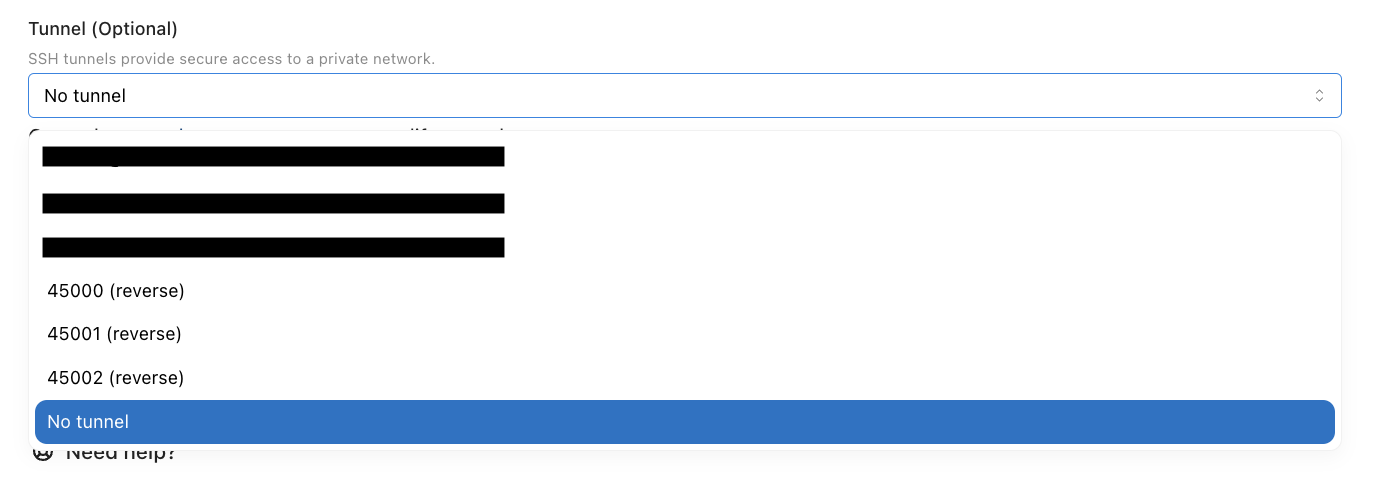
Using the reverse tunnel
Troubleshooting
Issue: Agent Stuck on Version Number During Startup
Issue: DNS Resolution Error During Integration
Last updated
Was this helpful?