Access requests
The Access requests feature in Secoda simplifies and centralizes the process of requesting, approving, and auditing access to data resources across multiple platforms. This feature helps organizations eliminate fragmented workflows, enhance security, and streamline compliance.
Access Requests are available to customers on Enterprise plan. Interested in upgrade options? Click on the "Upgrade" button on the Access Request page or reach out to the Customer team ([email protected]).
Key Features
Centralized Requests: Users can create Access requests directly within Secoda, specifying the resources, access duration, and roles.
Automated Provisioning & Revocation: Upon approval, access is provisioned automatically and revoked after the expiration period, reducing manual effort and improving security.
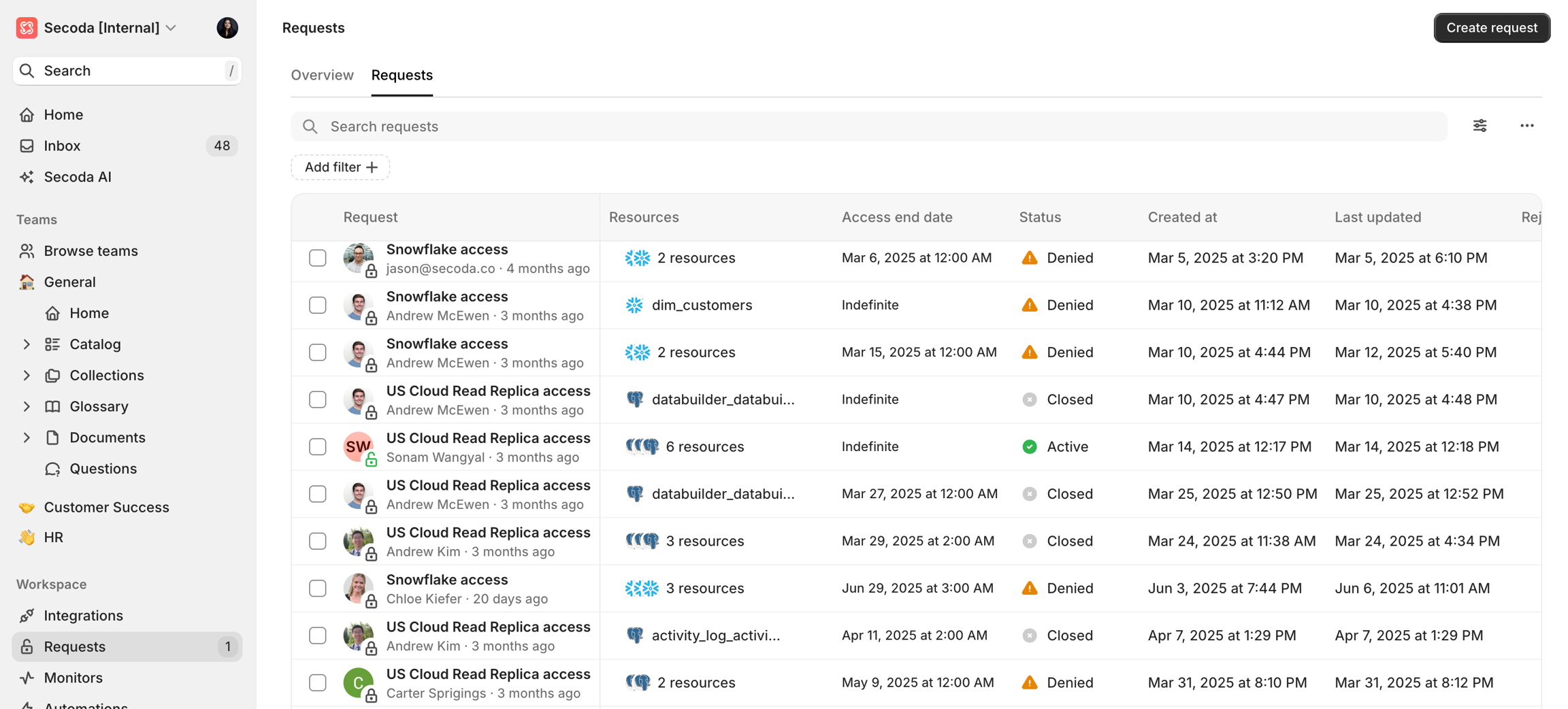
Detailed Audit Logs: Track every access request, including resources, requester, roles, reviewers, and expiration timelines, ensuring transparency and compliance.
Identity Management: Admins can browse and manage all ingested identities (users and roles) from integrated platforms.
Slack Integration: Configure a dedicated Slack channel for access request notifications. Approvals can be handled directly in Slack with a ✅ reaction.
Secoda AI Integration: Easily query Secoda AI to check if a specific user has access to a particular resource.
How It Works
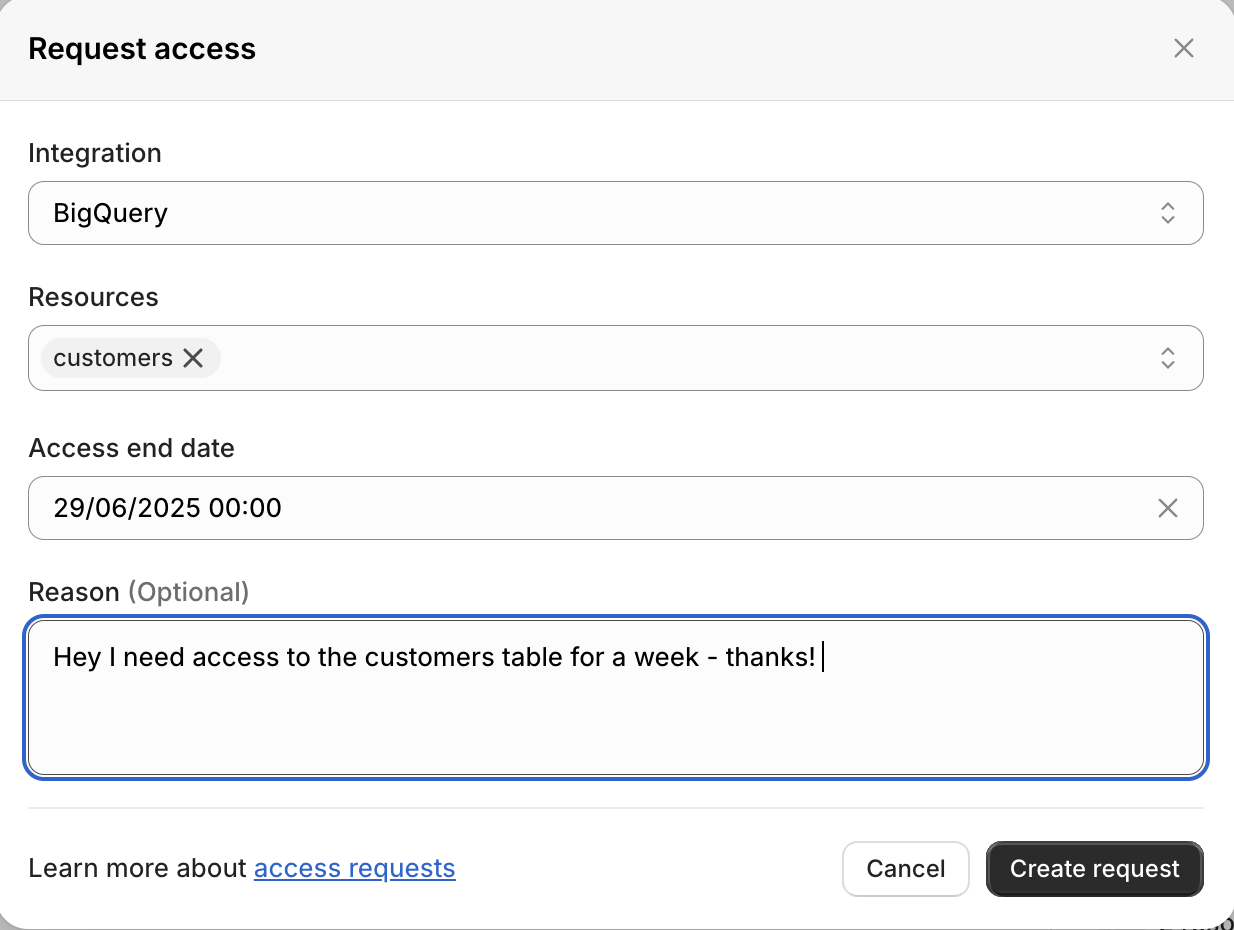
Creating a Request: Users can create an Access request from Secoda specifying:
Resources they want access to.
An optional reason for access.
An optional expiration period for access.
Review & Approval:
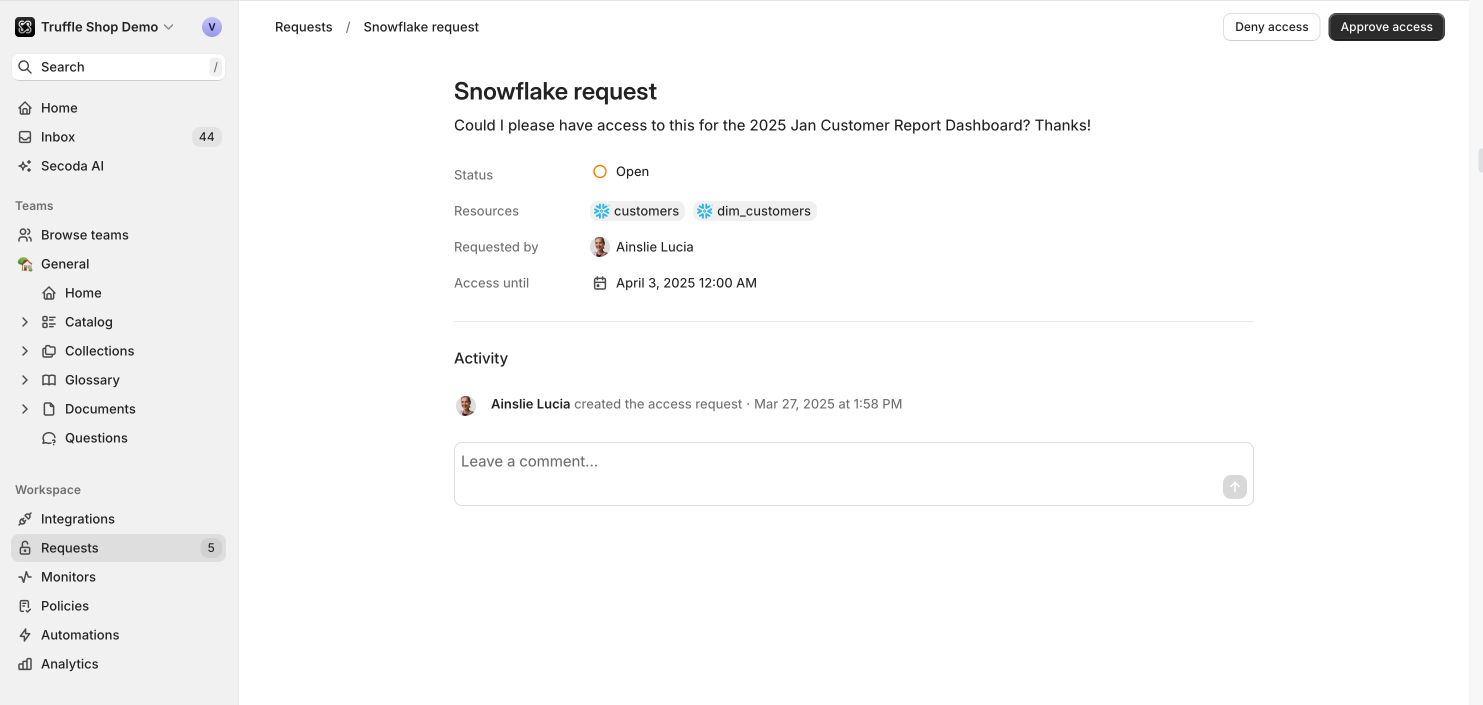
Reviewers evaluate the request and choose the role or identity to update.
Access requests can be approved via the Secoda interface or Slack.
Access Management: Upon approval:
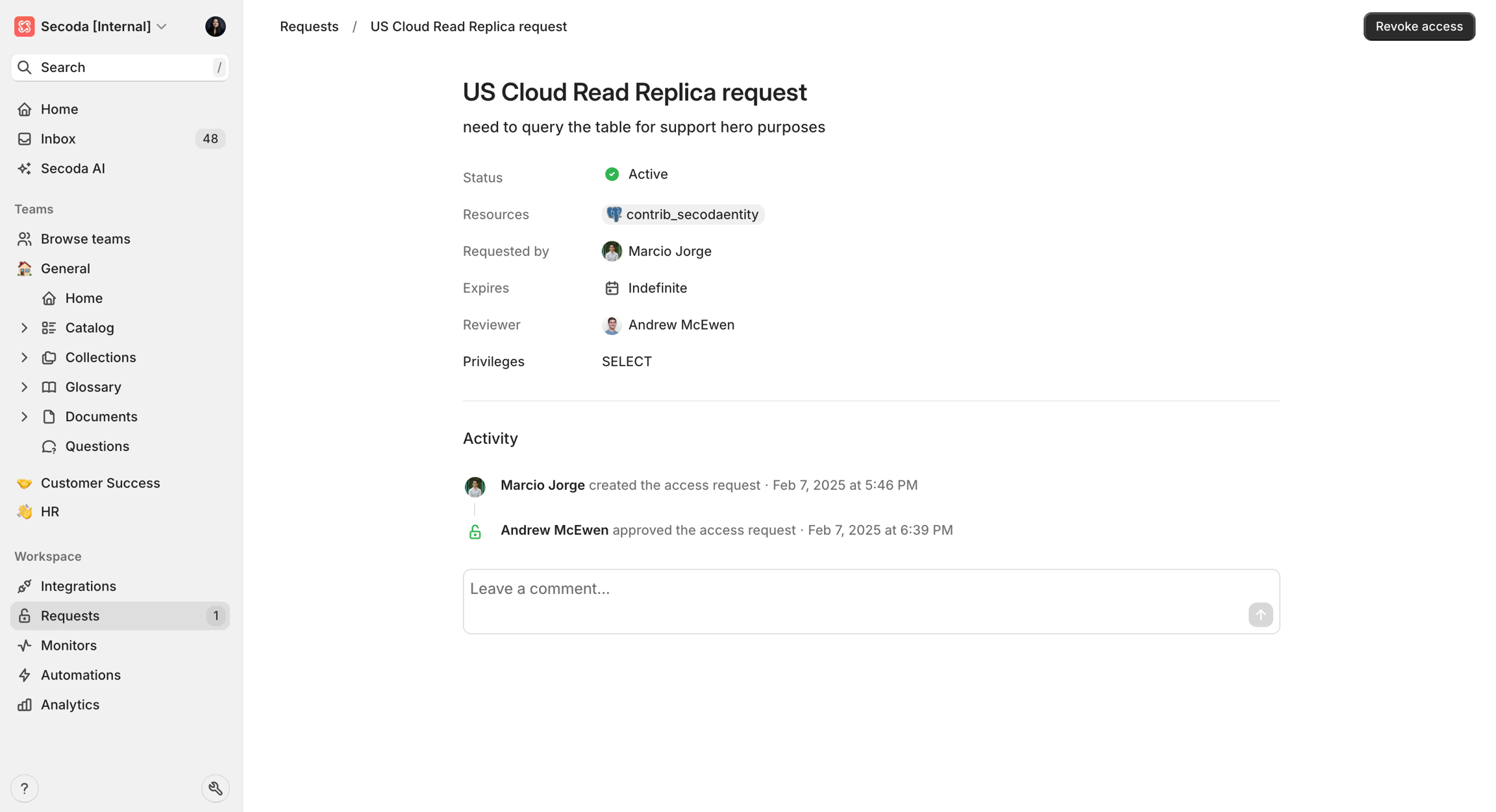
Access is granted automatically to the specified identity.
Access is revoked automatically after the expiration period.
Getting Started
Setup Integrations: Connect supported platforms to Secoda to ingest user and role identities.
Configure Slack Channel: Enable the “Access Requests” channel for real-time notifications and approvals.
Manage Roles: Assign the Reviewer role to appropriate team members to streamline the review process.
Track Requests: Use the Access Requests dashboard to monitor, audit, and manage requests.
Supported Integrations
Access Requests will be support the following platforms during the Beta period:
Snowflake
BigQuery
Redshift
Postgres
Use Cases
Data Access Governance: Ensure that only authorized users can access sensitive data and that access is tracked and time-bound.
Streamlined Collaboration: Simplify the process of granting access to analysts, data scientists, or other team members needing data for their workflows.
Enhanced Compliance: Maintain detailed audit trails for all access requests, meeting regulatory and organizational compliance needs.
Troubleshooting
No actions Availablefor certain requestsThere are no actions available for
ClosedorDeniedrequests.Activerequests can be revoked andOpenrequests can be approved, denied or deleted.
Last updated
Was this helpful?