SCIM
Manage users and groups from your identify provider.
Overview
Enterprise plan subscribers with SAML SSO enabled can opt to enable SCIM for their workspace. SCIM, or System for Cross-domain Identity Management, is an open standard that allows for the automation of user provisioning. If you have SAML SSO enabled with a supported identity provider, you can contact us to get SCIM enabled for your workspace.
Configure
To configure SCIM, you'll need to add a Token and URL to your SCIM provider.
The SCIM token is the API access token. As an Admin, you can generate one by navigating to Settings > API.
Your SCIM URL may be under a custom domain at https://<CUSTOM>/api/v2/scim/
Follow the directions below for your identity provider to setup the SCIM integration.
In the Okta admin pages, open the Secoda application you have for SAML 2.0
In the General tab, click Edit and choose SCIM in the Provisioning section and Save
In the Provisioning tab, enter the
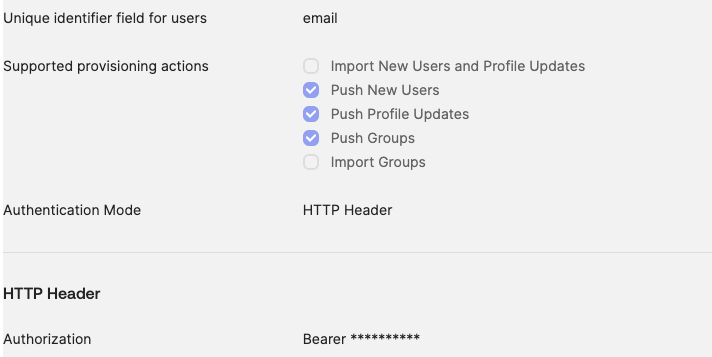
https://app.secoda.co/api/v2/scim/For the Unique identifier field for users section enter email
For Authentication mode field, choose HTTP Header and enter your Bearer token generated from your API settings in Secoda
For Supported provisioning actions only enable "Push New Users", "Push Profile Updates", "Push Groups"
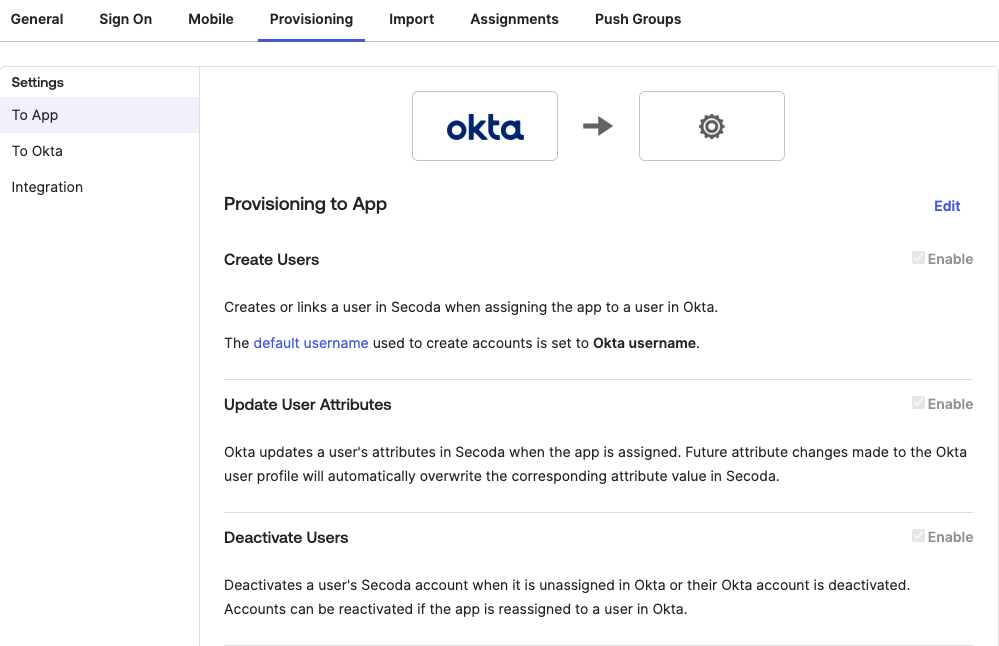
Then you may check the following Provisioning to App\
In OneLogin's Admin panel > Applications, click Add App
Search for the "SCIM Provisioner with SAML (SCIM v2 Enterprise, full SAML)" app and add
Click on the Configuration tab and add your SCIM base URL as
https://app.secoda.co/api/v2/scim/and the Bearer token generated from your API settings in Secoda.Click on the Provisioning tab and Enable Provisioning
Save your App
In Azure portal, go to Azure Active Directory -> Enterprise Applications.
Select an existing application or create a new one by searching for the specific application in the gallery.
In the application management screen, choose Provisioning in the left panel.
Under Provisioning Mode, select Automatic.
In Admin Credentials, enter the Tenant URL (e.g.,
https://app.secoda.co/api/v2/scim/) and a Secret Token generated from your API settings in Secoda.Expand Mappings and configure user attributes. Set mappings like
userPrincipalNametouserName,mailtoemails[type eq "work"].value, etc.Ensure Create, Update, and Delete actions are selected under Target Object actions.
Save the configuration
Okta Push Users and Groups
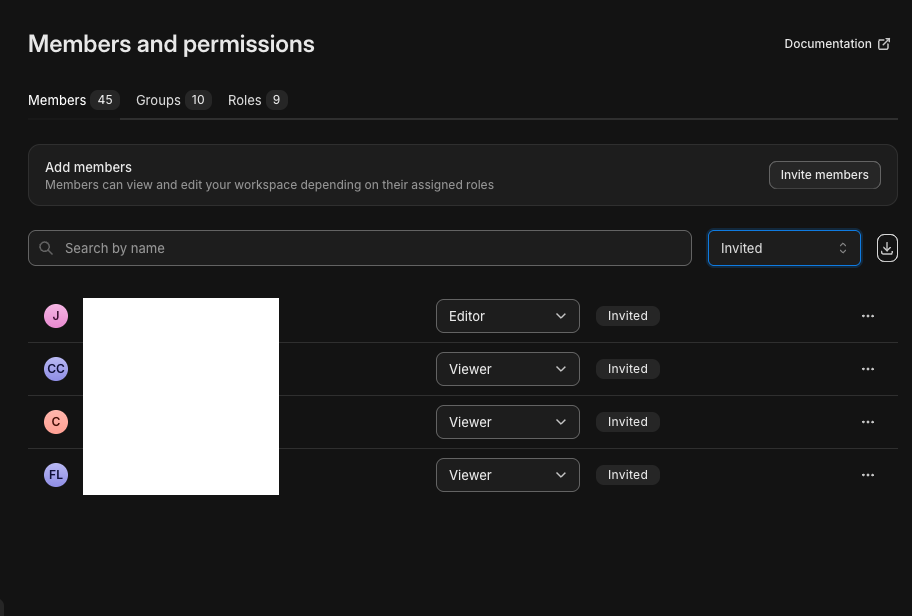
When users are assigned to your Okta application they will receive an invitation email to join Secoda. These users will be populated in Secoda in an "Invited" state. You must filter by "Invited" to see these users.
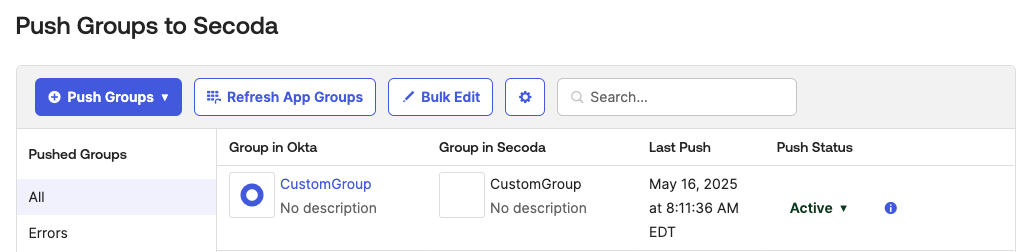
When Groups are pushed, they will appear under the "Groups" tab on "Members and permissions". "Invited" users will not appear as a group member until the user activates their account by signing in for the first time.
Advanced
Troubleshooting
Automatic provisioning of user <USER'S NAME> to app Secoda failed: Error while trying to push profile update for <EMAIL>: User not found
To resolve, unassign the user from the Okta application. Then reassign. This will ensure your Okta application has the correct user ID.
Provisioning Roles
To automatically provision roles via SCIM, create a custom attribute with external secodaRole under the urn:ietf:params:scim:schemas:core:2.0:User external namespace. You should then be able to assign roles (including custom roles) to users in Secoda via SCIM.
SCIM Groups endpoint
Secoda's SCIM integration also supports group syncing. From your side all you have to do is start pushing groups from your Identity provider to Secoda. These will then map one to one with Groups in Secoda.
When syncing groups, the following attributes are supported:
displayName: The name of the group in Secodamembers: Array of user references that belong to the group
SCIM Users endpoint
To add an active or disabled user using SCIM you can make a PUT request. Here is an example of how to use SCIM to add a user.
Setting "active": false will disable the user, while setting it to "active": true would activate the user.
Last updated
Was this helpful?